Qtr 1 | 2025
In this Issue:
-
The Buzz: AI Governance
-
service Highlight: Consulting Services for ai
-
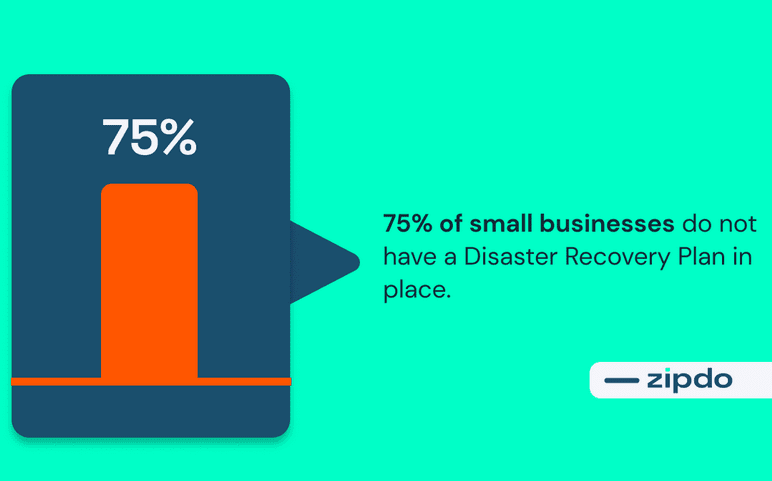
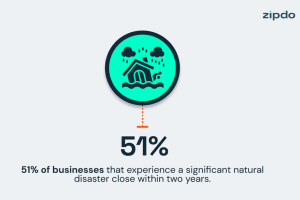
Business Stats: 2024 Small Business IT Statistics/Trends
-
Behind the Scenes: Birthdays, Anniversaries, Promotion!
-
Tech Tips and Tricks: Microsoft MFA Enforcement for all users
ePress Archive
QTR 4 | 2024
THE BUZZ – AI Governance
AI Risks for Small Businesses
Security Threats, Intellectual Property Theft, Policy Gaps
As small businesses increasingly adopt AI technologies, they face critical risks surrounding security, intellectual property protection, and policy management. This article highlights these challenges and underscores their profound implications for businesses in today’s competitive environment.
Security Vulnerabilities
Data Breaches
Data breaches pose a significant threat, particularly when AI systems that manage sensitive information become prime targets for cybercriminals. The consequences of these breaches can be devastating, leading to substantial financial losses, legal repercussions, and severe damage to an organization’s reputation. Alarmingly, 43% of cyberattacks focus on small businesses, which face an average breach cost of $2.98 million (Verizon, IBM 2021). Organizations must recognize the urgency of safeguarding their data and take proactive measures to prevent such costly incidents.
AI Model Attacks
Adversarial AI model attacks pose a significant threat, capable of manipulating outputs and undermining critical decision-making processes, ultimately resulting in substantial financial losses. Alarmingly, a report by Microsoft (2020) reveals that 25% of businesses leveraging AI have fallen victim to security breaches, highlighting the urgent need for strengthened defenses against such threats.
Insider Threats
Insider threats pose a significant risk, as employees misusing AI systems can lead to devastating data leaks, legal liabilities, and costly investigations. A study by Verizon in 2020 revealed that 30% of data breaches are perpetrated by internal actors. This highlights the urgent need for organizations to safeguard against insider threats and bolster their security measures.
Intellectual Property (IP) Theft
AI-Generated IP Vulnerabilities
The vulnerability of AI-generated intellectual property (IP) stems from ambiguous ownership, which can jeopardize unique assets and trigger costly legal disputes. Remarkably, between 2013 and 2019, patent applications related to AI surged by an astonishing 175% (WIPO). This significant rise underscores the urgent need for clear guidelines and protections in the rapidly evolving landscape of AI technology.
Industrial Espionage
Industrial espionage represents a grave threat involving the illicit theft of vital business intelligence concerning artificial intelligence (AI). Such acts can result in significant losses of competitive advantage and market share for companies. Interestingly, the Commission on the Theft of American Intellectual Property estimates that intellectual property theft costs the U.S. economy an astounding $600 billion annually. This staggering figure underscores the urgent need for robust measures to safeguard against such threats and protect the integrity of American innovation.
Internal AI Policies
Undefined AI Governance
The absence of strong AI governance can lead to inconsistent applications, ethical failures, and significant quality control challenges. Only 30% of companies have established an AI ethics policy (KPMG 2020). This highlights a critical gap that must be addressed to ensure responsible and effective AI deployment.
Inadequate Employee Training
Insufficient employee training and a shortage of AI skills can result in critical tool misuse, costly errors, and heightened vulnerability to cyberattacks. Alarmingly, 55% of businesses cite a lack of AI skills as a major barrier to adoption (O’Reilly, 2021). Organizations must prioritize training to harness AI effectively or risk falling behind in an increasingly competitive landscape.
Compliance Risks
Non-compliance with AI regulations represents a significant compliance risk that can result in severe penalties, unexpected retroactive costs, and disruptions to business operations. With the increasing importance of regulatory adherence, it is anticipated that by 2024, 75% of large enterprises will invest in hiring AI specialists to safeguard their brand and reputation (Gartner). Embracing this proactive approach is crucial for navigating the complex landscape of AI governance and protecting the future of their businesses.
Mitigation Strategies
- Invest in AI-specific cybersecurity measures.
- Develop strategies to protect AI-generated IP.
- Establish comprehensive internal AI governance policies.
- Provide ongoing AI training for employees.
- Stay informed about and enforce compliance with AI regulations.
By proactively addressing these risks, small businesses can harness the power of AI more effectively, positioning themselves for success while minimizing potential downfalls in today’s fast-evolving technological landscape.
Solution Highlight – Business continuity
business Continuity is the ability to maintain critical functions in the event of an emergency or disruption.
Arcserve Wins
Best Business Continuity and Best Data Backup & Recovery Solutions Company for 2024!
Business Stats: 2024 SMall business STATISTICS & trends
Keeping up with the latest trends is crucial for small business owners to stay informed, improve productivity, understand customers, and drive sustainable growth in the ever-changing business landscape. The business statistics below will provide an insightful overview of small businesses in 2024.
Your DCR Team – Behind the Scenes
Birthdays
Welcome the newest member of the DCR family, baby Karson!
Anniversaries
Tech Tip – Identifying Fake Mobile Apps
 Fake apps are created to harm users and their devices
Fake apps are created to harm users and their devices
These apps are designed to look legitimate but carry out malicious activities such as monitoring your activities, installing malware, showing annoying ads, or stealing your personal information.
Fake apps can be dangerous and involve ad bots, billing fraud, botnets, hostile content, hostile downloads, phishing, privilege escalation, ransomware, rooting, spam, spyware, and trojans.
To spot fake apps, check the reviews, look for grammar errors in the app description, research the developer, check the number of downloads, review the permission agreement, check the update frequency, and scrutinize the app icon.
Be wary of apps with low ratings, numerous user complaints, or uniformly positive reviews, which could be fake. Watch out for grammatical errors in the app description. Check the number of downloads and the release date. Research the developer to determine if they are reputable. Read the permission agreement before downloading an app, and be cautious of apps that ask for unnecessary authorizations. Apps that update too frequently may have security vulnerabilities. Finally, scrutinize the app icon, as fake apps often display icons similar to those of the actual app they are copying.